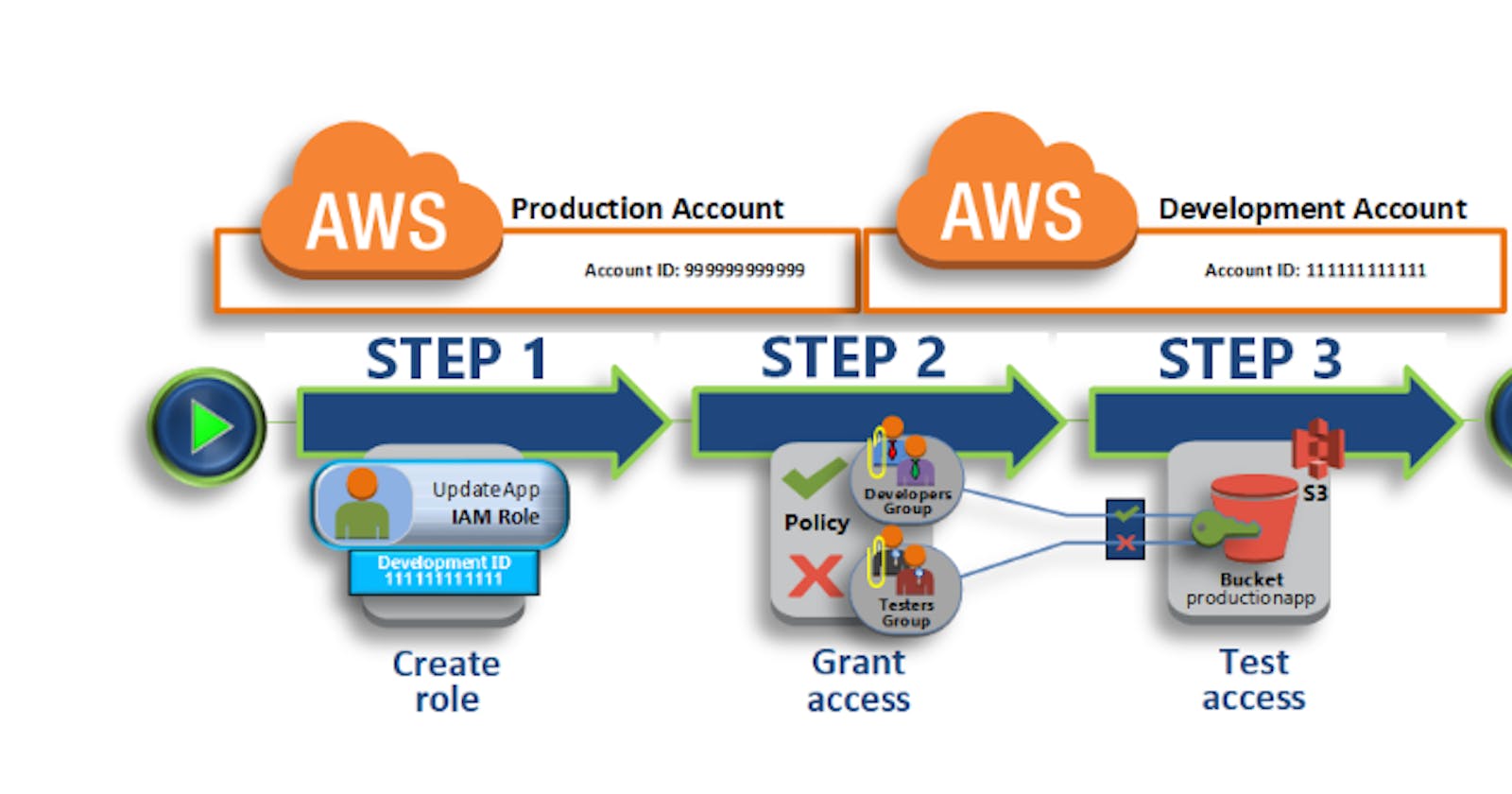
AWS IAM is a service offered by Amazon Web Services (AWS) that enables you to securely control access to AWS resources. It allows you to manage users, groups, roles, and permissions within your AWS account.
Users: A user is an identity within your AWS account that can be associated with a person or an application. Users can be granted specific permissions to access and interact with AWS resources.
Groups: Groups are collections of users. By assigning permissions to a group, you can efficiently manage the permissions for multiple users simultaneously. Users with similar kinds of permissions are typically grouped into IAM Groups. This approach helps to simplify the management of permissions and access control.
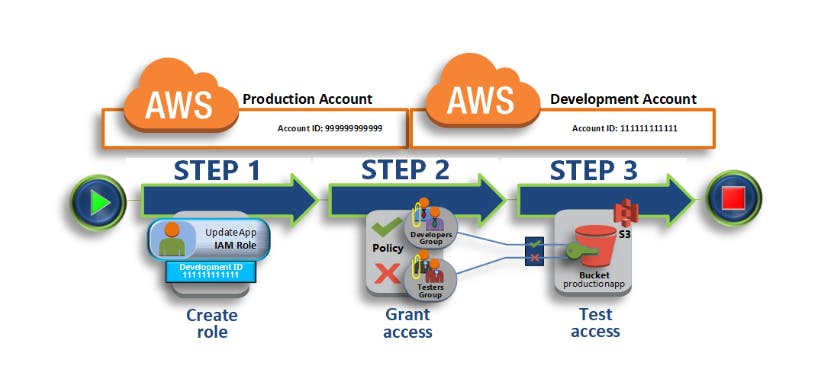
Roles: Roles are similar to users, but they are intended to be assumed by authenticated entities, such as applications, services, or other AWS accounts. Roles provide a secure way to delegate access across different AWS resources or accounts.
Policies: Policies are JSON documents that define permissions. They specify what actions are allowed or denied on which AWS resources. Policies can be attached to users, groups, or roles to grant or restrict access.
Identity Providers: AWS IAM supports identity providers, such as corporate directories or web identity providers (e.g., Amazon, Google, Facebook), allowing you to manage user identities outside of AWS and grant them temporary access to AWS resources.
Usage Example
You are the AWS admin, responsible for managing the entire cloud infrastructure for your company. As the admin, you have complete control over AWS IAM (Identity and Access Management), which is the powerful service that governs access to AWS resources.
On the first day of onboarding a new employee or setting up access for an application, you create an IAM user within your company's AWS account. This user represents their identity inside the AWS ecosystem.
However, you don't just hand out full access willy-nilly – that would be a security nightmare! Instead, you organize users into IAM groups, which are like different departments or teams within your AWS infrastructure.
Each group has specific policies attached to it, and these policies are like rulebooks that define what actions members of that group are permitted to perform on which AWS resources. For example, the "DevOpsEngineers" group might have a policy allowing them to launch and manage EC2 instances, while the "Developers" group has access to deploy code to specific S3 buckets.
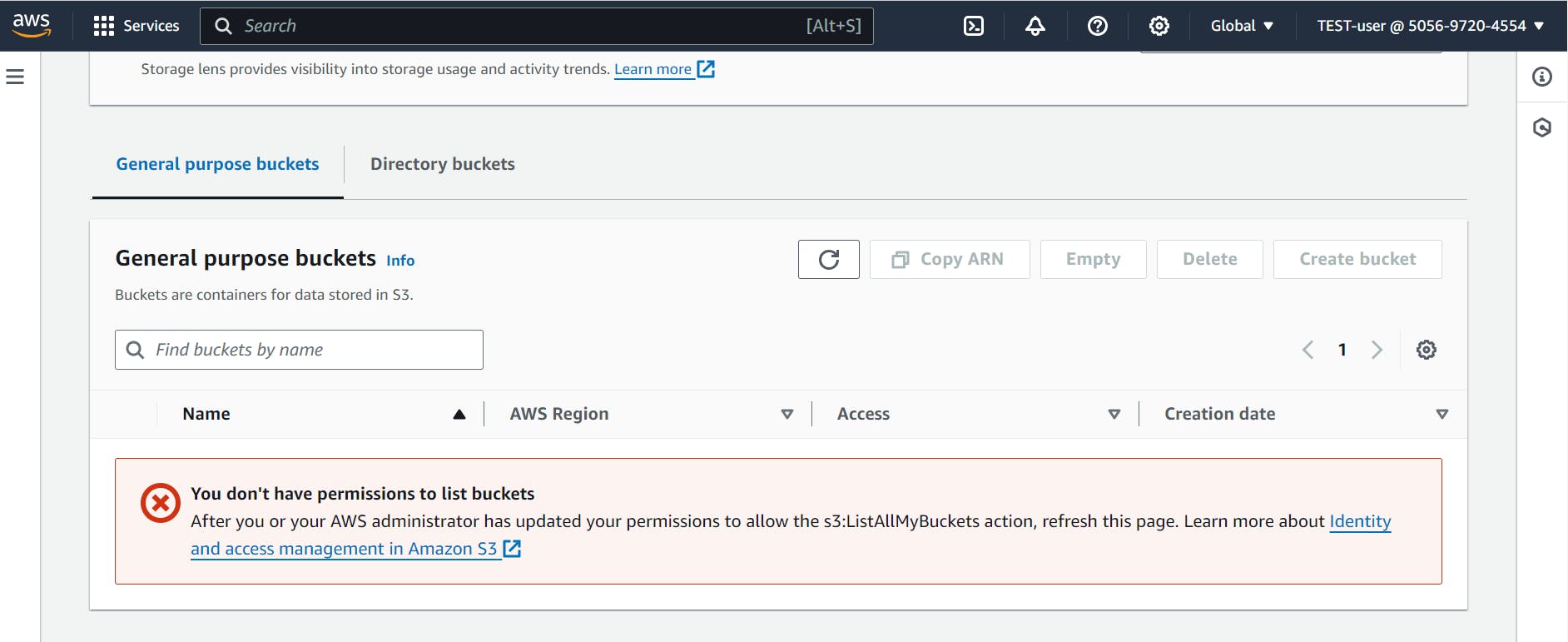
The test user has specific permissions.
As the admin, you assign users to the appropriate groups based on their roles and responsibilities within the company. When you add a user to a group, they automatically inherit all the permissions defined in that group's policies.
Now, whenever a user tries to interact with an AWS resource, like launching a new EC2 instance or accessing an S3 bucket, the IAM service acts as a gatekeeper. It checks the policies associated with that user's identity (the groups they belong to) and either grants them access if they have the right permissions or denies them if they don't.
By leveraging IAM groups and policies, you can efficiently manage permissions for different roles within your organization, such as DevOps engineers, developers, data analysts, and more. It's like setting up customized workstations for each team, giving them the right tools and access they need to do their job, while keeping everything secure and under your control as the admin.